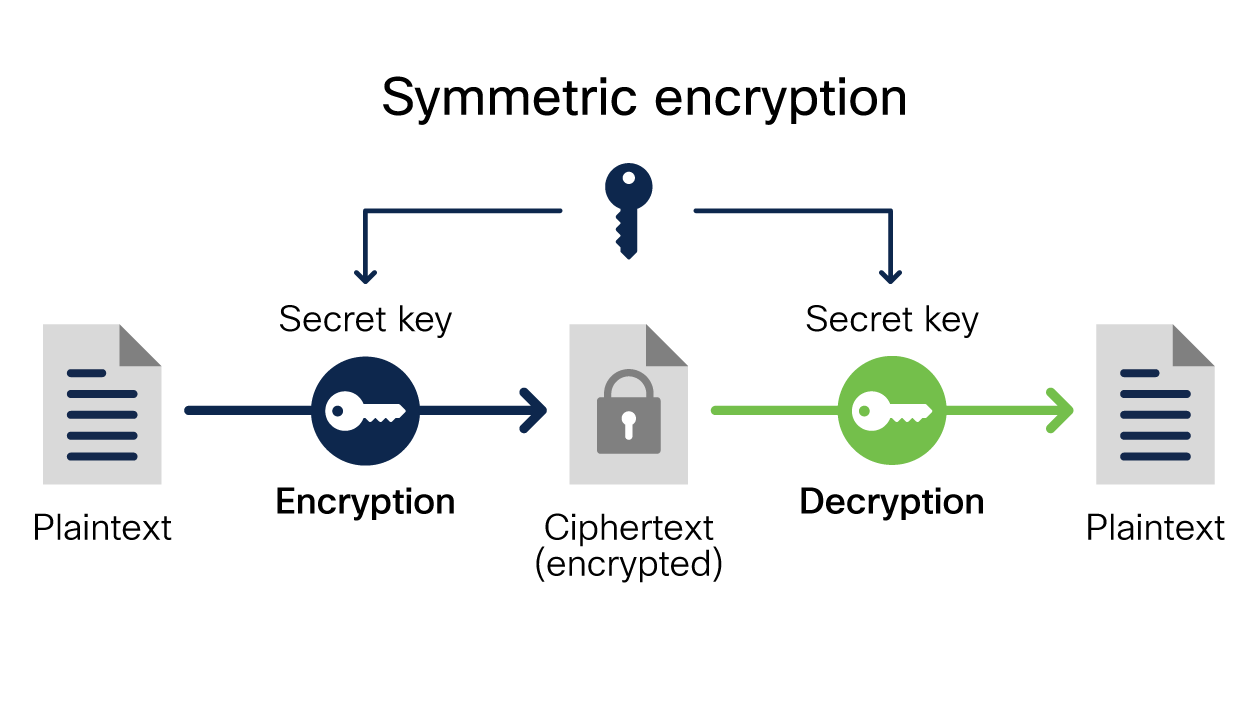
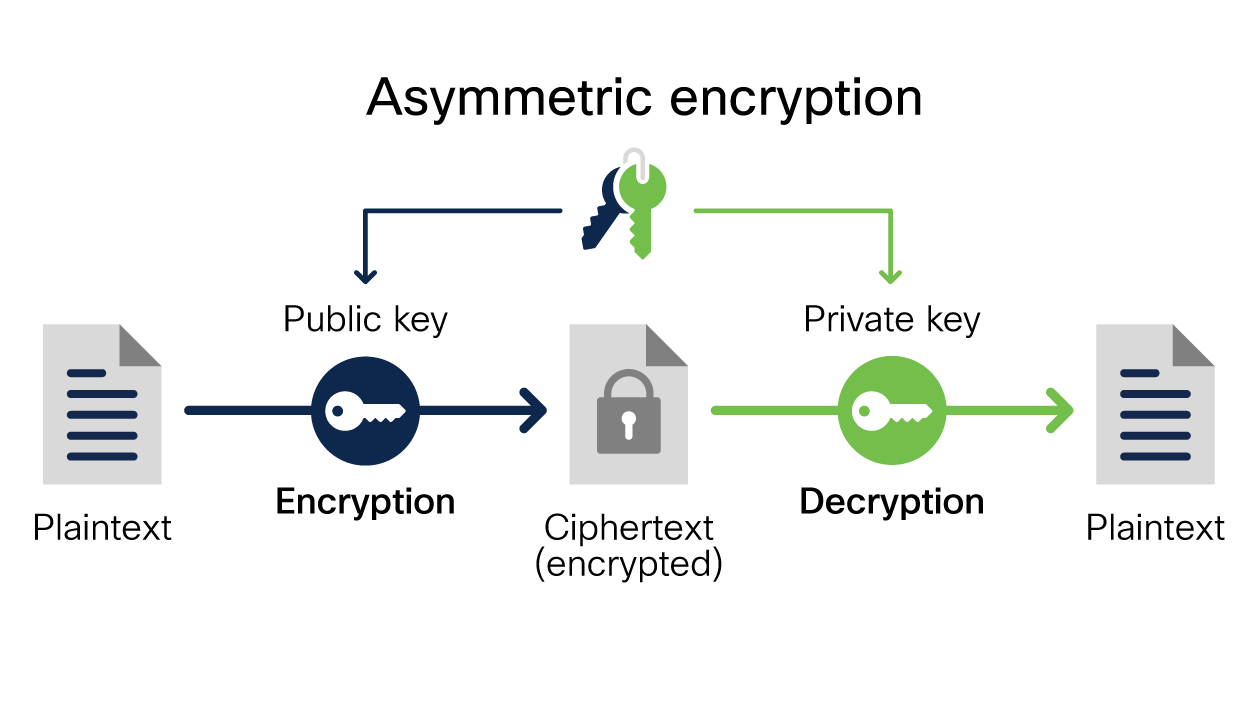
Why should we care about encryption?
Every time we make a purchase online, use the bank ATM, text or call somebody, encryption keeps the transaction or communication private and highly secure. Encryption provides a layer of security so information is only accessed by the authorized users. It has become an essential part of our modern day lives. We should care about encryption as it provides privacy, security, integrity of data, and authentication. In many cases it is required for regulatory compliance.
What encryption algorithms should I use?
This is a complicated question to answer. When deciding on an encryption algorithm, it is important to consider these questions:
- Is this algorithm up to date?
- Has this algorithm been through a validation process?
- Does the OS, application, or hardware support the encryption?
If any question cannot be answered in the affirmative, either a new algorithm should be chosen or more research should be done.
Because encryption is a constantly changing field, these decisions can be difficult. However, it is important to understand that encryption is very important to security. Making decisions based on partial knowledge about encryption can be dangerous. If you don't fully understand encryption, make sure you are using crypto designed and built by someone who does understand.
How do I send an encrypted email?
To properly encrypt emails, businesses should invest in encryption tools designed for email. When choosing the tools, a business can decide on sender encryption or key management.
- Sender encryption provides tools for users to encrypt their emails, such as flagging as "urgent" or installing a plug-in with a clickable encryption button. In sender encryption, however, businesses are relying on the judgement of employees to decide what should be encrypted.
- Key management is typically a central system and set of rules that will act and encrypt emails. This central host can use big data to accurately encrypt sensitive data and information.
How do I detect encrypted threats?
While businesses are encrypting traffic to protect their data, attackers are encrypting threats. As Cisco CEO Chuck Robbins said at Cisco Live, "70 percent of the attacks that are launched are within encrypted traffic."
Decrypting all traffic, however, would be incredibly time consuming. Businesses must invest in tools that leverage big data to identify potential threats. Machine learning and network analytics can flag obscure indicators and behaviors that suggest an encrypted threat. Once identified, the network can quarantine and investigate the threat before damage occurs.